Most people agree that there are benefits to the individual in having an ID card when they need to establish their identity. The privacy problems with ID cards do not come from the ID card itself, but from data collected about an individual by different organisations and then collated using the ID card number as the link between different sets of data.
A solution to the problem is to remove any possibility of a link between the ID card and other data. One way this can be done and to protect privacy is to use an identity provider in a system with the following characteristics:
- Assume we have a national ID card with limited information of photograph, name and date of birth. It has a chip with an encrypted identification number. There is no visible ID number.
- Identification cards are voluntary but may be required for certain activities, such as air travel, where a person has to be physically present and it is important to establish his or her identity.
- We make it impossible and illegal to store ID card information in other data repositories without the individual’s permission.
- Each individual has a set of online authenticated verified identifying data that they control, they supply and which requires their permission to access. We call this, together with the programs that manipulate the data, an 'edentiti'.
- When an organisation needs information about a person then the edentiti, with permission from the individual, gives the minimum information needed and gives a new number that the organisation is to use for identification. Thus an individual is known by a different number in different organisations which is in turn is different from the ID card encrypted number.
Advertisement
The following diagram illustrates how such a system will protect privacy and yet still allow the convenience of an identification card.
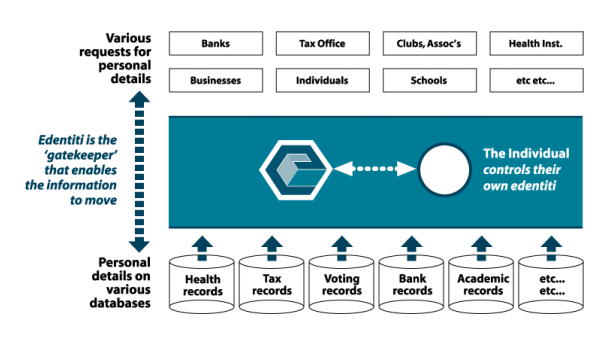
In this system an ID card is just another data store like a bank record. It has a particular purpose which is to be a portable identification device in much the same way as we use a driver's licence.
The advantage of this system is that data about an individual is kept in separate data stores that can ONLY be linked through edentiti where the individual controls all accesses. This permits the individual to keep control and more important, to know what information others hold on them. This contrasts with the current situation where organisations can get information about you from a variety of sources without your knowledge and worse - collate the data.
Edentiti is a system which protects privacy by the individual taking control over their own identity. It is an instance of what the IT industry calls an identity provider. Identity providers are part of an open standards movement to remove anonymity from the Internet in cases where anonymity is a problem.
Using any identity provider, including edentiti, is voluntary. That is, you do not have to have one - but if you want particular services then you can use it as a way of establishing who you are.
Advertisement
Edentities are created in much the same way that people now get 100-point authenticated accounts with a bank. The difference is that an individual creates their online identity and has full control over it and it includes more than a record of paper documents. An edentiti includes biometrics of face and voice prints, secrets such as pin numbers and identifiers of things the individual owns, such as phone numbers. It also belongs to the individual and not to some other organisation like a bank. The 100 points and other information are checked by an independent party so others can be confident you are who you say you are.
Once you have an edentiti you can use it for many purposes. For example, you can use it to make an electronic signature on an online form. Assume you have an edentiti, assume you have stored a secret pin, and assume you have stored your telephone number on edentiti. When you click on “sign here”, edentiti calls you on your phone and asks you to enter your pin number, which you do. It is the same as a written signature as you have to both possess the phone and know the pin number to make your electronic mark. How secure you want to make it depends on what you are prepared to store in your edentiti. It may be that your voice print has to match, or that an image of you on a webcam, has to match your stored picture.
Another use is for edentiti to deliver your credentials to a prospective employer. What happens with edentiti is that you ask the university or educational institution to deliver the appropriate documents to the prospective employer. They receive your credentials directly from the institution rather than from you - but it is all under your control.
Discuss in our Forums
See what other readers are saying about this article!
Click here to read & post comments.
12 posts so far.